Cybercriminals create new advanced social engineering tactics and target small and medium-sized businesses. For example, the FBI estimates that cybercriminals stole more than $28 billion through email fraud from 2016-2020, with an average loss per incident of more than $150,000.
Social engineering fraud involves tricking employees into divulging sensitive information or assisting in a fraudulent scheme. Business owners and IT professionals must be vigilant in identifying and preventing these attacks to minimize exposure.
As these social engineering tactics continue to evolve, business owners and IT professionals must adapt their cybersecurity approach to mitigate the risks. Identifying and preventing these attacks is essential to protect your business and your clients’ sensitive information.
Cyber insurance can provide an additional safeguard against these risks by providing coverage for losses resulting from cyber-attacks.
Understanding Social Engineering Attacks
While phishing and other online crimes have been problems for businesses for many years, social engineering fraud is increasingly leveraging information from corporate sources, including social accounts, to target companies, vendors, and executives.
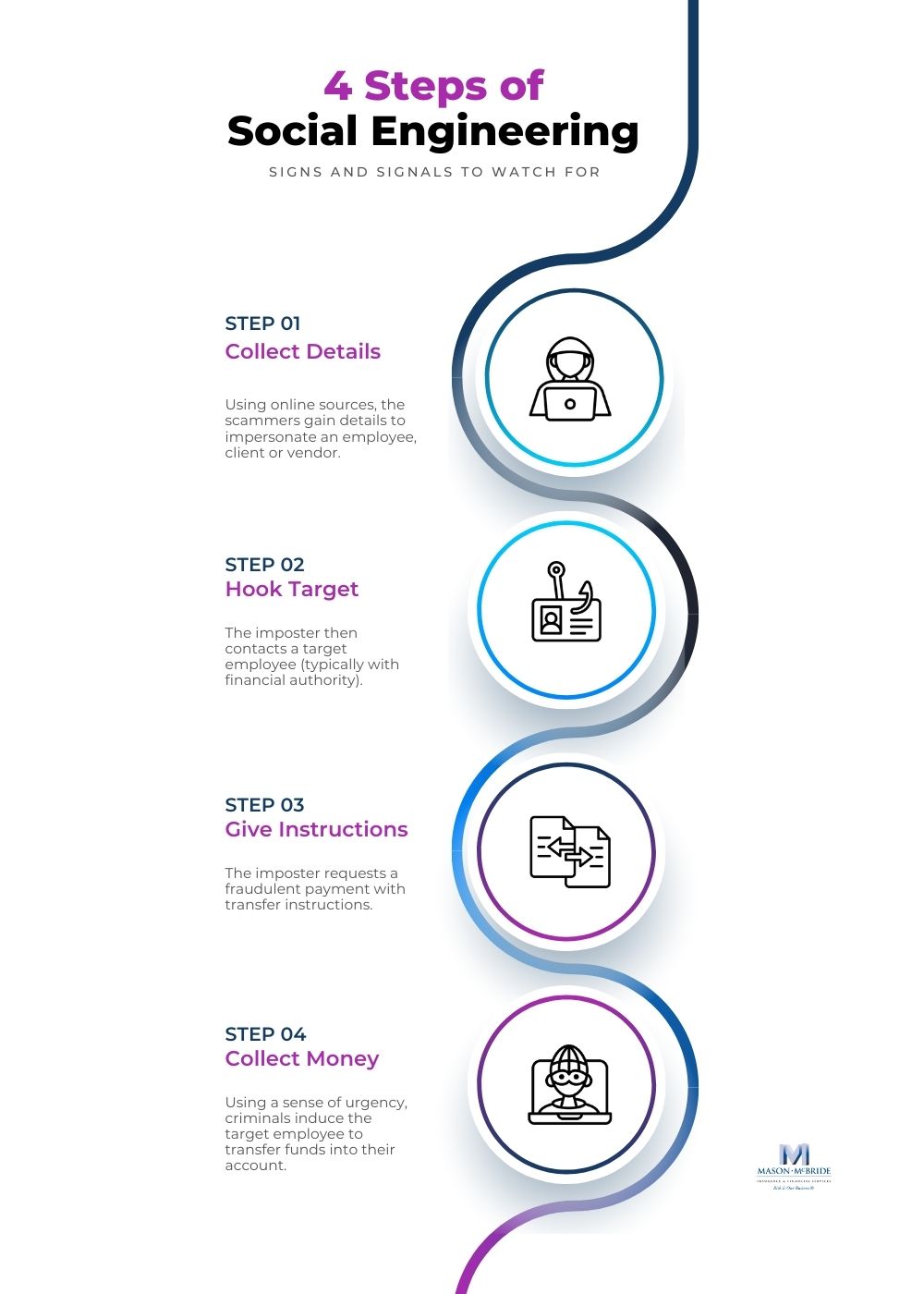
Social engineering can be described as the art of human hacking by impersonating executives, employees, vendors, and suppliers.
Social engineering, in its basic form, is tricking an individual into providing commercial or personal information, usually done through technology.
However, unlike technical hacking, which is designed to gain access to systems or data, social engineering scams exploit a human weakness, curiosity, and anxiety through deception to manipulate them to use the information gathered for fraudulent purposes.
The most common social engineering attack is the unintended payment or transfer of funds made to cyber scammers through this deception.
Real-Life Example: A Social Engineering Claim Scenario
Consider this claim example of a social engineering scam on a business:
The company accountant receives an email from the CEO that looks legitimate but is fake and includes a link to a login page where the hacker harvests company credentials.
The cybercriminal then uses the credentials to log in and transfer funds from the company bank account to an illegitimate bank account.
In this scenario, because the cybercriminal gets credentials and gains unauthorized and persistent access to company assets until discovered and stopped, financial loss and expenses could trigger the Computer and Funds Transfer Fraud coverage (FTF) if all other conditions for FTF are met.
Claim Scenario provided by Cowbell
Understanding Social Engineering Attacks
- Baiting – attackers lure users into a trap that steals their personal information.
- Scareware – users are deceived into thinking their system is infected with malware.
- Pretexting – attackers obtain user information through a series of cleverly crafted lies.
- Phishing – attackers forward an email or text to the target seeking information that might help with a more significant crime.
- Spear Phishing – attackers tailor their message based on job positions in contacts belonging to the victim to make their attack less conspicuous.
- Tailgating – attackers closely following an authorized person into a restricted access area to commit a crime.
The Growing Risk: Why Social Engineering Remains a Leading Threat
Post-COVID-19, more and more businesses are working remotely and moving more information to the cloud. As a result, phishing is at an all-time high and is still the most successful social engineering threat.
Phishing continues to increase at alarming rates. The scammers use new apps that can easily evade network security. The most common companies impersonated by phishers are Microsoft, Google, Facebook, Apple, and PayPal.
According to the FBI’s Internet Crime Complaint Center, BEC attacks (Business Email Compromise attacks) have increased by over 2,370% since 2015. The scammer’s email will look authentic and appear from a known authority figure, compelling the employee to open the email and act upon the request.
Since BEC attacks don’t involve malware based on social engineering tactics, they also can evade antivirus and spam filters.
As a result, the expectation is that companies will invest more in their front lines of defense, such as education, training, and implementing multi-factor authentication. Moreover, most insurance companies will no longer provide cyber coverage to a company without multi-factor authentication.
New Threats: Deepfakes and Nation-State Actors
Emerging risks include the use of deepfake technology and activity from nation-state actors. These techniques can be used to spread disinformation, impersonate executives, and manipulate communications for fraudulent purposes.
While deepfake-related fraud is still developing, its potential to undermine credibility and trigger financial or reputational harm is significant. Awareness and layered defenses are essential.

Cyber Insurance: A Component of Your Risk Strategy
Cyber liability insurance may help offset the costs associated with a cyber incident—both first-party (like forensic investigations, notification, and credit monitoring) and third-party claims (such as alleged unauthorized disclosure of data).
Coverage varies by insurer and policy, but many offer access to breach response resources, including attorneys, forensic teams, and public relations professionals. As part of a broader cybersecurity program, cyber insurance helps companies manage financial exposure from incidents not typically addressed under standard property or liability policies.
Steps You Can Take Today
- Educate employees regularly on phishing and social engineering tactics.
- Implement multi-factor authentication across email and system access points.
- Limit publicly available information that could be leveraged in impersonation attacks.
- Review your current insurance program to determine if social engineering is covered, and under what conditions.
- Develop an incident response plan to reduce response time in the event of an attack.
Learn More About Cyber Coverage Options
At Mason-McBride, we help businesses explore cyber insurance solutions that align with their operations and risk profile. To learn more or request a proposal, our team is here to assist.
For helpful tips on other popular topics, check out articles on:
- Cyber Insurance Exclusions
- Decoding E&O Insurance Policy Language
- Ransomware Developments
- Cybercrime Targeting Small Businesses
Article By Jamie Parry
